Installing the nRF Sniffer¶
The nRF Sniffer for Bluetooth LE software consists of firmware that is programmed onto a nRF52840 MDK USB Dongle and a capture plugin for Wireshark that records and analyzes the detected data.
This section of the documentation explains how to install the nRF Sniffer for Bluetooth LE software.
Programming the nRF Sniffer firmware¶
You must connect a nRF52840 MDK USB Dongle running the nRF Sniffer firmware to your computer to be able to use the nRF Sniffer for Bluetooth LE.
The nRF Sniffer firmware in .uf2-format is located in firmware/ble_sniffer/.
Download the latest firmware and complete the following steps to flash the firmware:
-
Push and hold the button and plug your dongle into the USB port of your computer. Release the button after your dongle is connected. The RGB LED turns green.
-
It will mount as a Mass Storage Device called UF2BOOT.
-
Drag and drop
nrf_sniffer_for_bluetooth_le_<version>.uf2onto the UF2BOOT volume. The RGB LED blinks red fast during flashing. -
Re-plug the dongle and the nRF Sniffer will start running.
Button Changed after programmed
The button will be configured as RESET functionality after programmed with the sniffer firmware. The next time you want to enter UF2 Bootloader mode, just double-click the button after plugged the dongle. If you want to change the button to GPIO functionality, try the button sample in NCS guide.
Installing Wireshark¶
To install Wireshark for your operating system, complete the following steps:
- Go to the Wireshark download page.
- Click the release package for your operating system from the Stable Release list. The download starts automatically.
- Install the package.
- Download the Wireshark standard package or the latest stable PPA for Ubuntu Linux distribution from the Wireshark download page.
- Install the package on your computer.
- Answer
yeswhen the installer asks you if non-superusers should be able to capture packets. This ensures that packet capture is available to all users in the wireshark system group. - Add the correct user to the wireshark user group. For example, type
sudo usermod -a -G wireshark $USER. - Add the correct user to the dialout user group. For example, type
sudo usermod -a -G dialout $USER. - Restart your computer to apply the new user group settings.
Installing the nRF Sniffer capture tool¶
The nRF Sniffer for Bluetooth LE software is installed as an external capture plugin in Wireshark.
To install the nRF Sniffer capture tool, complete the following steps:
-
Install the Python requirements:
- Open a command window in the
tools/ble_sniffer/extcap/folder. -
Install the Python dependencies listed in
requirements.txtby doing one of the following: -
Close the command window.
- Open a command window in the
-
Copy the nRF Sniffer capture tool into Wireshark's folder for personal external capture plugins:
- Open Wireshark.
-
Go to Help > About Wireshark (on Windows or Linux) or Wireshark > About Wireshark (on macOS).
-
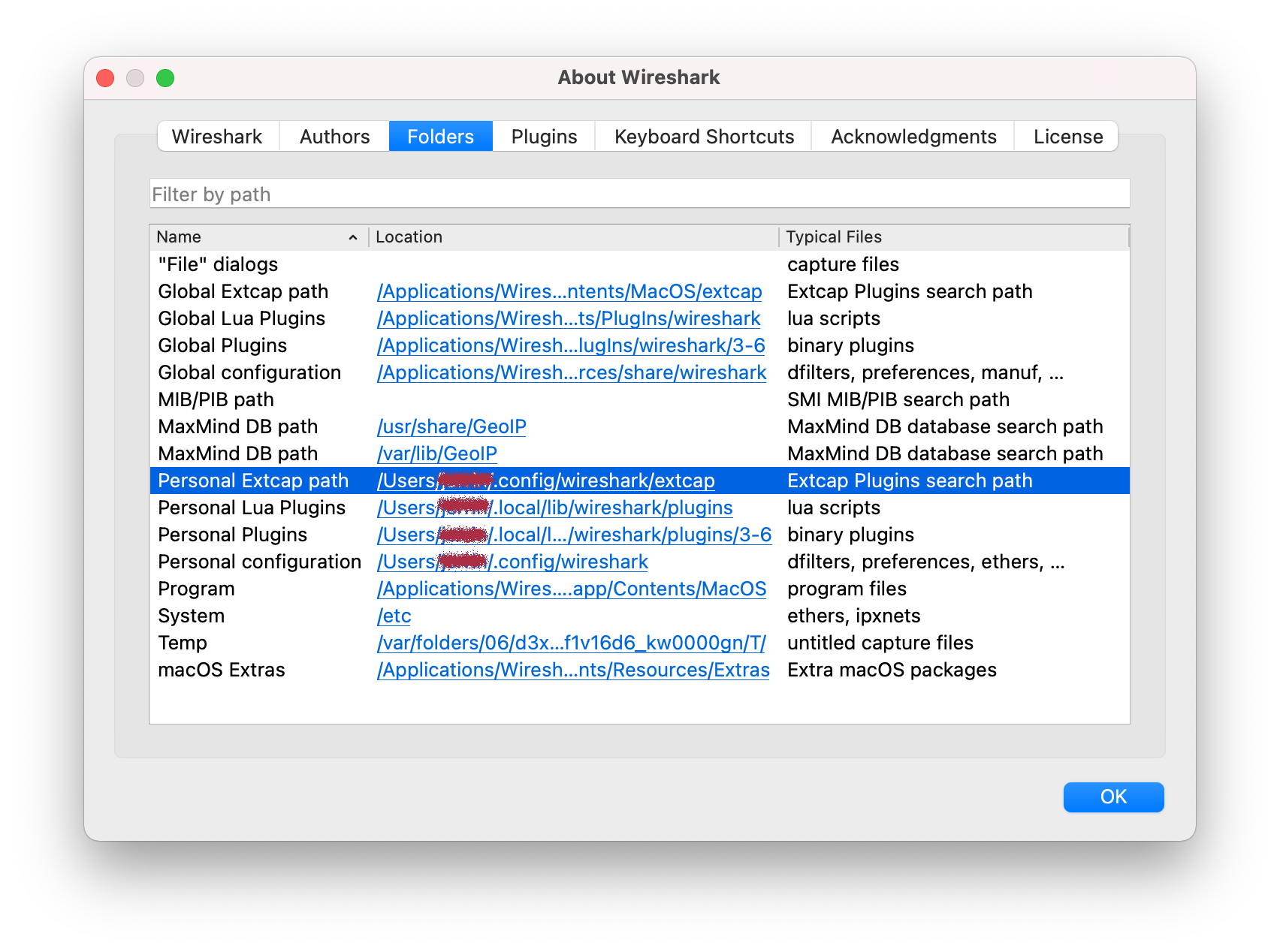
Select the Folders tab.
-
Double-click the location for the Personal Extcap path to open this folder.
-
Copy the contents of the
tools/ble_sniffer/extcap/folder into this folder.
-
Make sure that the nRF Sniffer files can be run correctly:
- Open a command window in Wireshark's folder for personal external capture plugins.
-
Run the nRF Sniffer tool to list available interfaces.
You should see a series of strings, similar to what is shown in the following:
-
Enable the nRF Sniffer capture tool in Wireshark:
-
Refresh the interfaces in Wireshark by selecting Capture > Refresh Interfaces or pressing F5 . You should see that nRF Sniffer is displayed as one of the interfaces on the Wireshark capture screen.
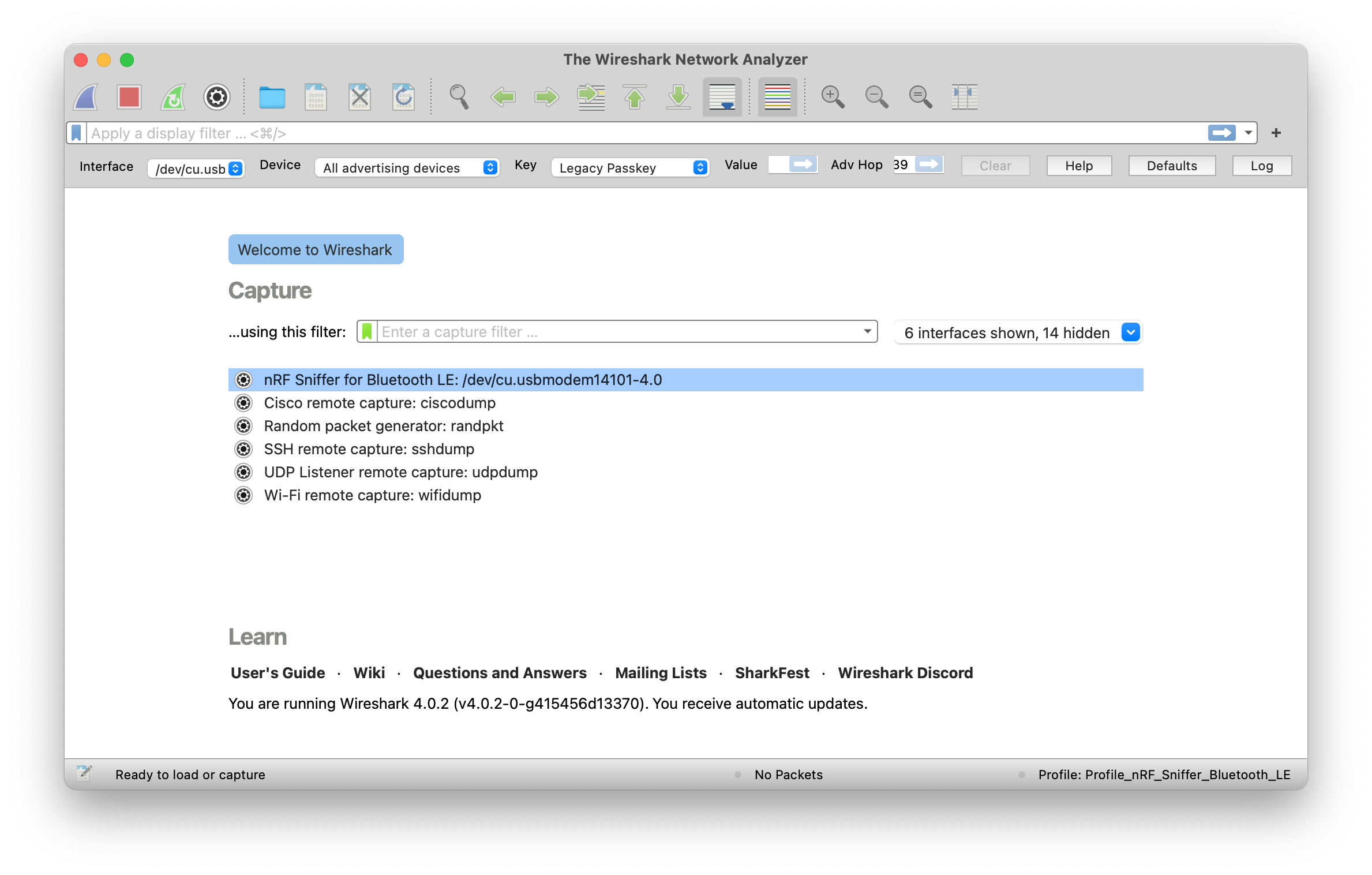
-
Select View > Interface Toolbars > nRF Sniffer for Bluetooth LE to enable the nRF Sniffer interface.
-
Adding a Wireshark profile for the nRF Sniffer¶
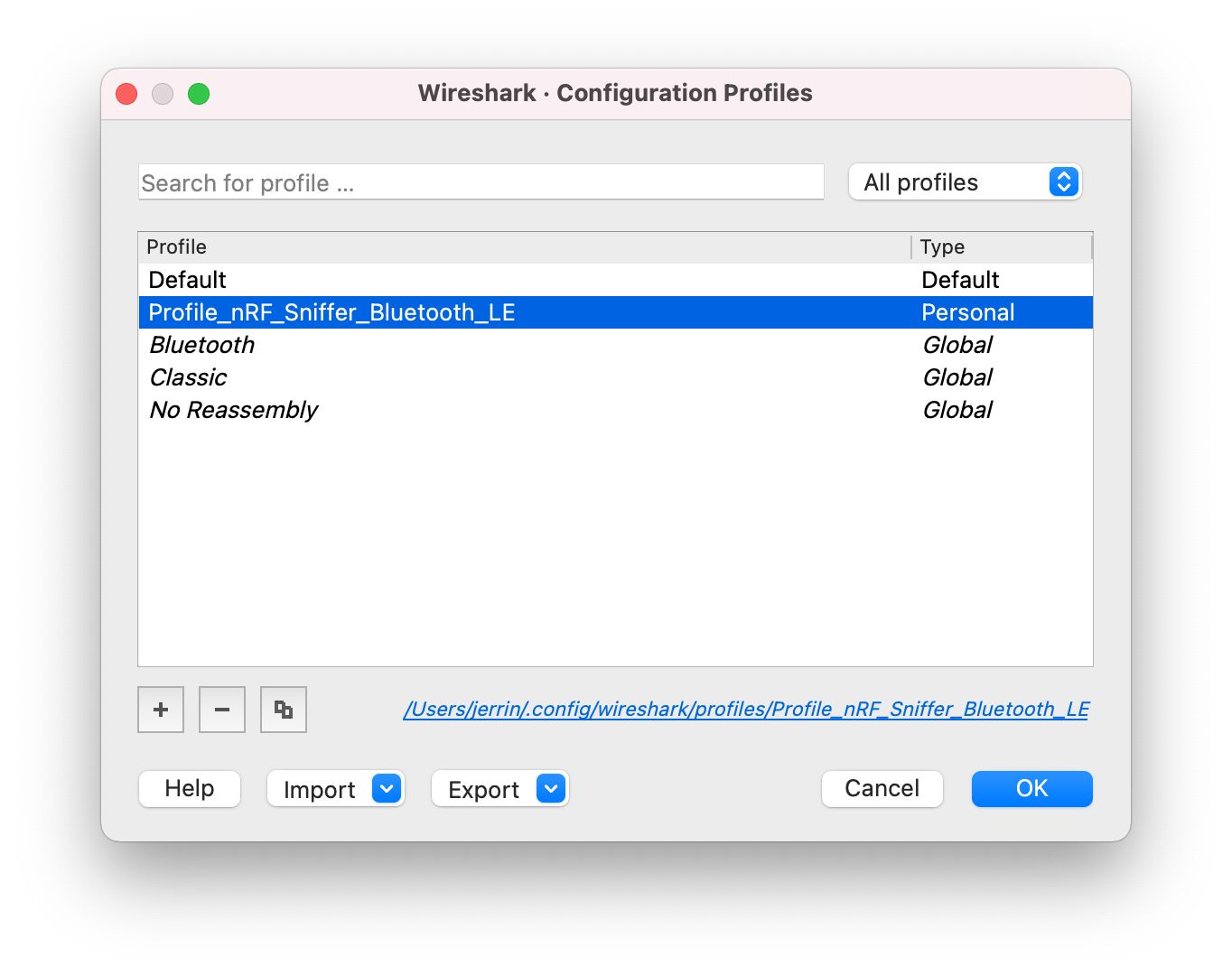
You can add a profile in Wireshark for displaying the data recorded by the nRF Sniffer for Bluetooth LE in a convenient way.
To add the nRF Sniffer profile in Wireshark, complete the following steps:
- Go to Help > About Wireshark (on Windows or Linux) or Wireshark > About Wireshark (on macOS).
- Select the Folders tab.
- Double-click the location for the Personal configuration to open this folder.
- Copy the profile folder
tools/ble_sniffer/Profile_nRF_Sniffer_Bluetooth_LEinto theprofilessubfolder of this folder. - In Wireshark, select Edit > Configuration Profiles....
-
Select Profile_nRF_Sniffer_Bluetooth_LE and click OK.