Configuring Wireshark for the nRF Sniffer¶
The nRF Sniffer for 802.15.4 must be configured for capturing and analyzing packets exchanged on Thread and Zigbee networks.
Configuring Wireshark for Thread¶
Capturing packets on a Thread network requires configuring at least the IEEE 802.15.4 decryption keys. Additionally, you can also configure the CoAP port and the 6loWPAN settings.
Configuring decryption keys for Thread¶
You must configure IEEE 802.15.4 decryption keys to decode packets exchanged on the network and display the data in a readable format.
You need to know the Thread decryption key before you start configuring it in Wireshark. For example, if one of the devices in the Thread network has the OpenThread CLI enabled, you can check the decryption key by calling the masterkey CLI command.
To configure the decryption keys:
- In Wireshark, go to Edit > Preferences... (on Windows or Linux) or Wireshark > Preferences... (on macOS).
-
In the Preferences section list, go to Protocols > IEEE 802.15.4.
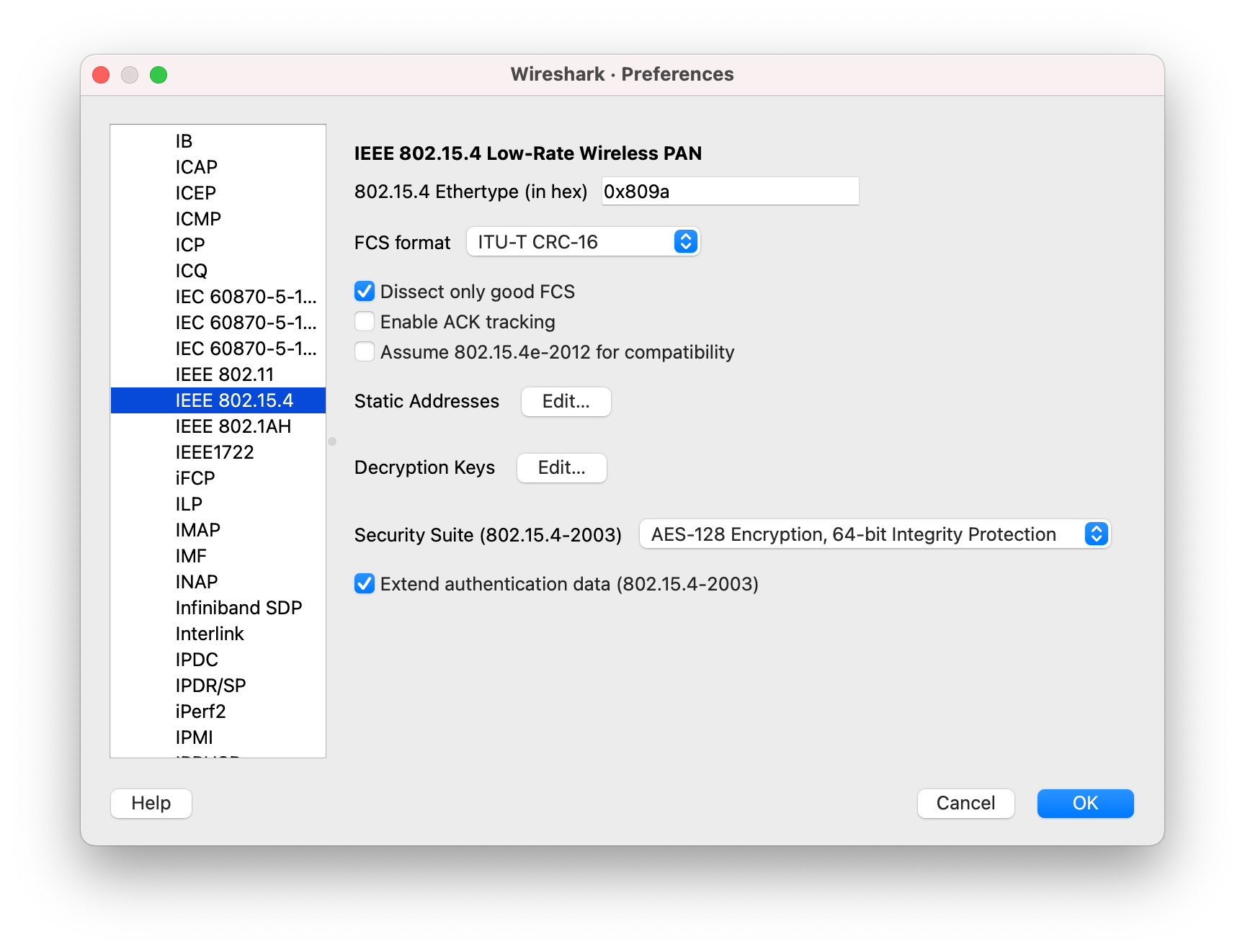
-
Click the Edit... button next to Decryption Keys.
-
In the Keys window:
-
Click + and add the Decryption key value with Decryption key index set to
0and Key hash set toThread hash.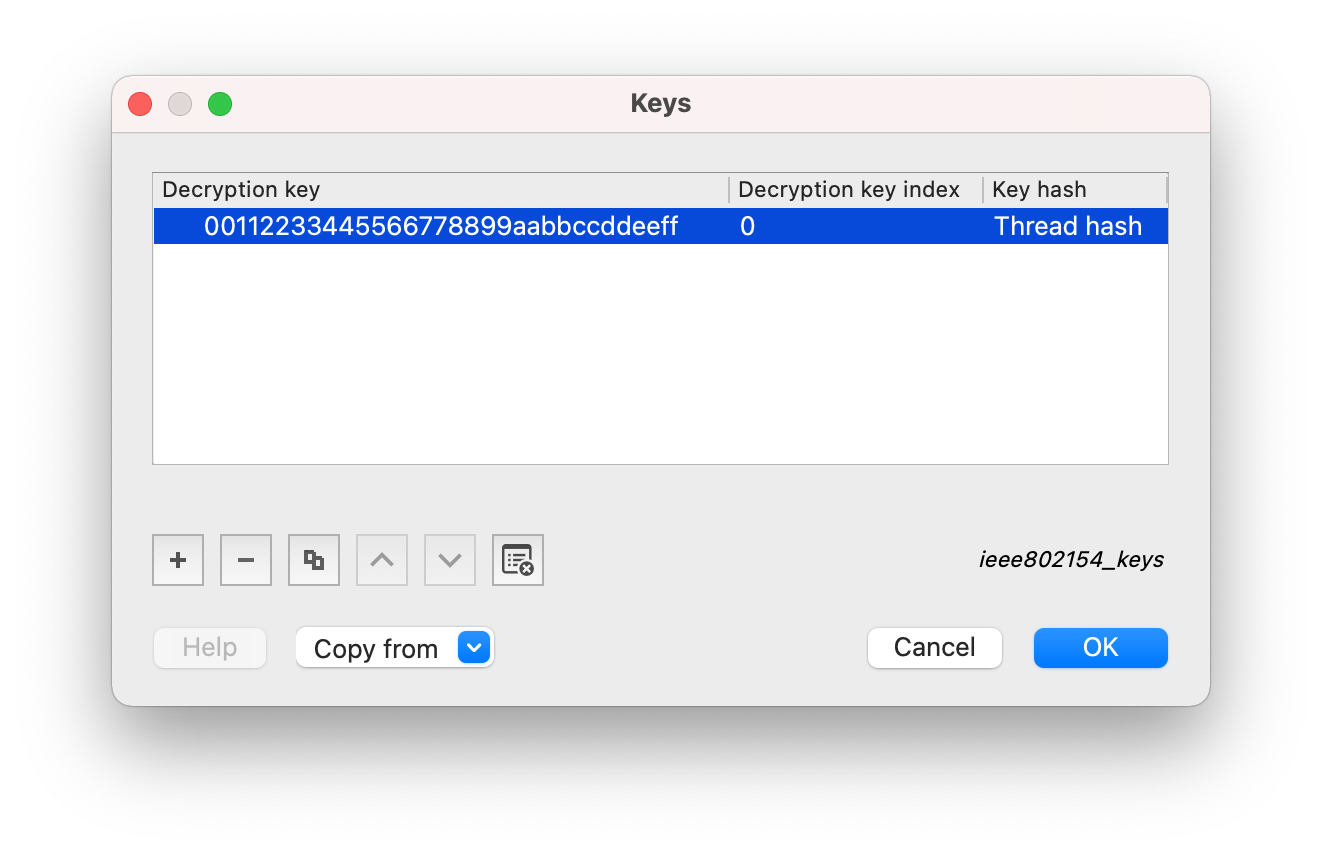
-
Click OK to close the window.
-
-
Click OK to save the decryption keys for Thread.
Configuring CoAP port for Thread¶
The Thread network uses the CoAP protocol on port 61631 for network management. You must configure this port in Wireshark if you want to correctly decode network management packets sent over this port.
Configuring CoAP port using Decode As¶
You can apply the CoAP protocol settings once on a per-capture basis using the Decode As option.
To configure the CoAP port using this option:
- In Wireshark, go to Analyze > Decode As....
-
In the Decode As... settings window, click the + button to add a new entry with the Field set to UDP port, Value set to 61631, and Current set to CoAP.
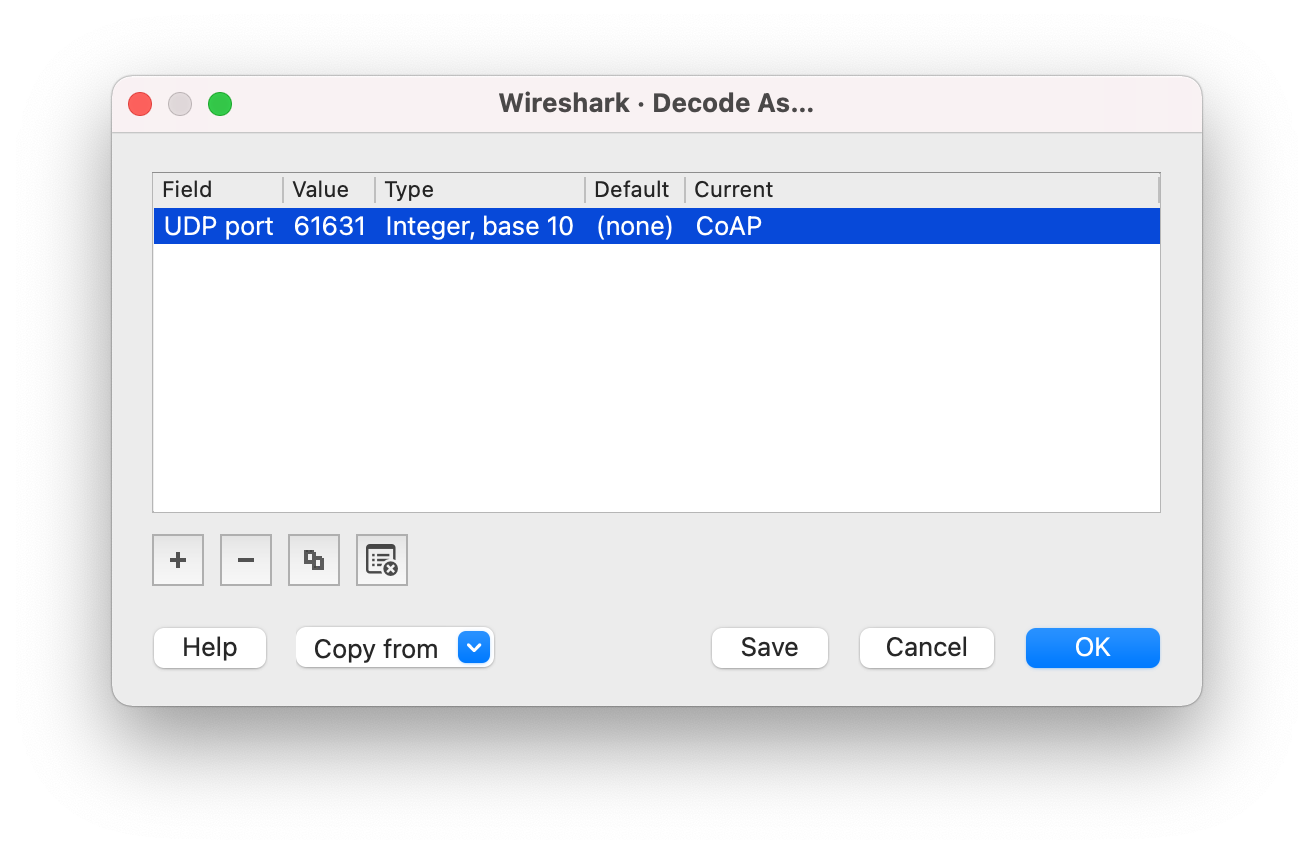
-
Click OK to save the Decode As... settings.
Configuring CoAP port using Preferences¶
You can apply the CoAP protocol settings globally by defining the CoAP port number in Wireshark Preferences.
To configure the CoAP port using this option:
- In Wireshark, go to Edit > Preferences... (on Windows or Linux) or Wireshark > Preferences... (on macOS).
-
In the Preferences section list, go to Protocols > CoAP.
-
Set the CoAP UDP port to
61631. - Click OK to save the CoAP port settings.
Configuring 6loWPAN context¶
6loWPAN defines contexts that are used to shorten IPv6 addresses sent over-the-air. Configuring the 6loWPAN context ensures that the correct IPv6 address is displayed during packet analysis.
You can configure different 6loWPAN contexts depending on the Thread Network Data.
To configure the 6loWPAN contexts used by Thread examples:
- In Wireshark, go to Edit > Preferences... (on Windows or Linux) or Wireshark > Preferences... (on macOS).
- In the Preferences section list, go to Protocols > 6loWPAN.
-
Set the following contexts to the provided values:
- In the Context 0 field, add
fdde:ad00:beef:0::/64. - In the Context 1 field, add
fd11:22::/64.
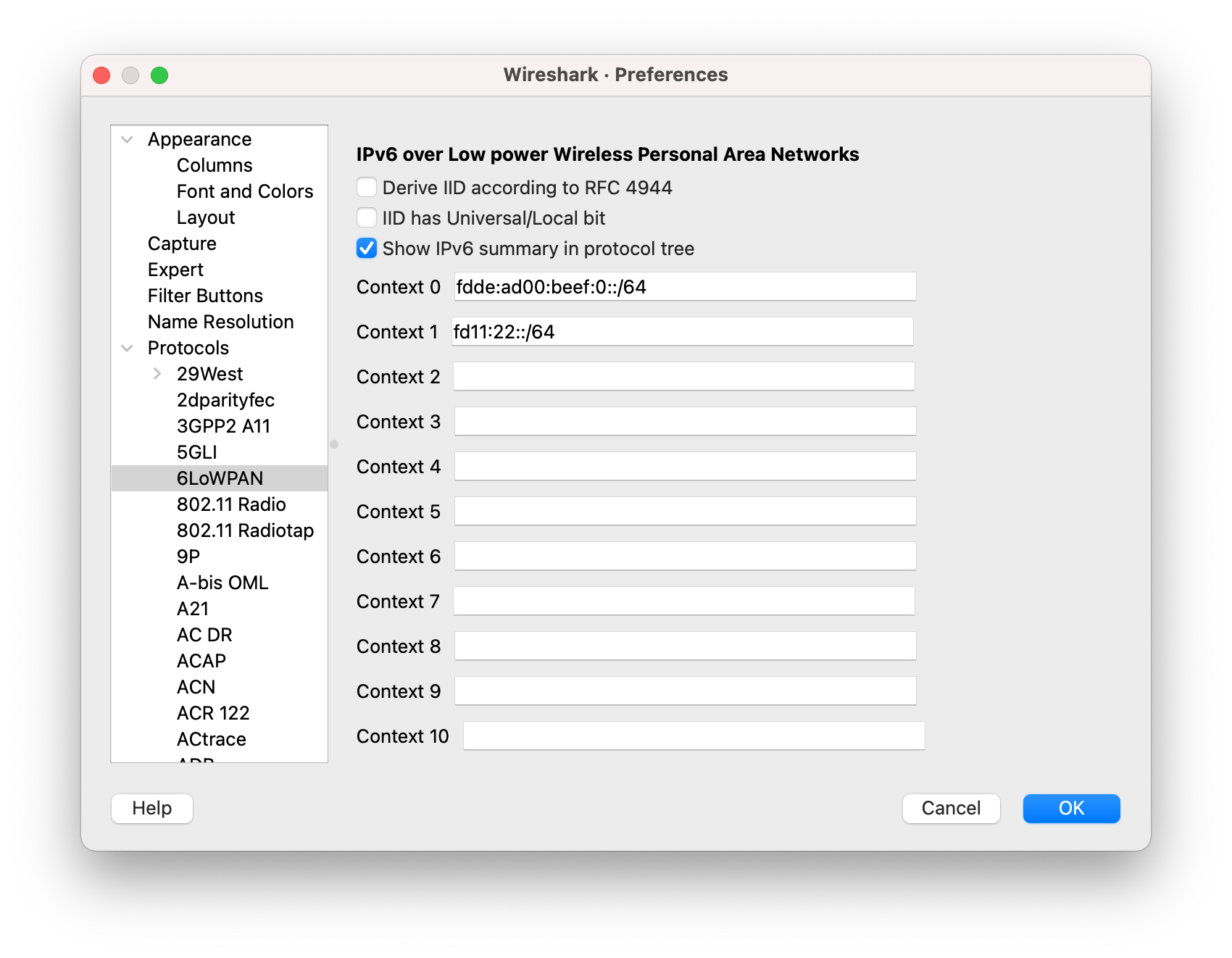
- In the Context 0 field, add
-
Click OK to save the 6loWPAN contexts for Thread.
Disabling unwanted protocols¶
If Wireshark uses incorrect dissectors to decode a Thread message, you can optionally disable unwanted protocols.
To disable unwanted protocols when capturing data from a Thread network:
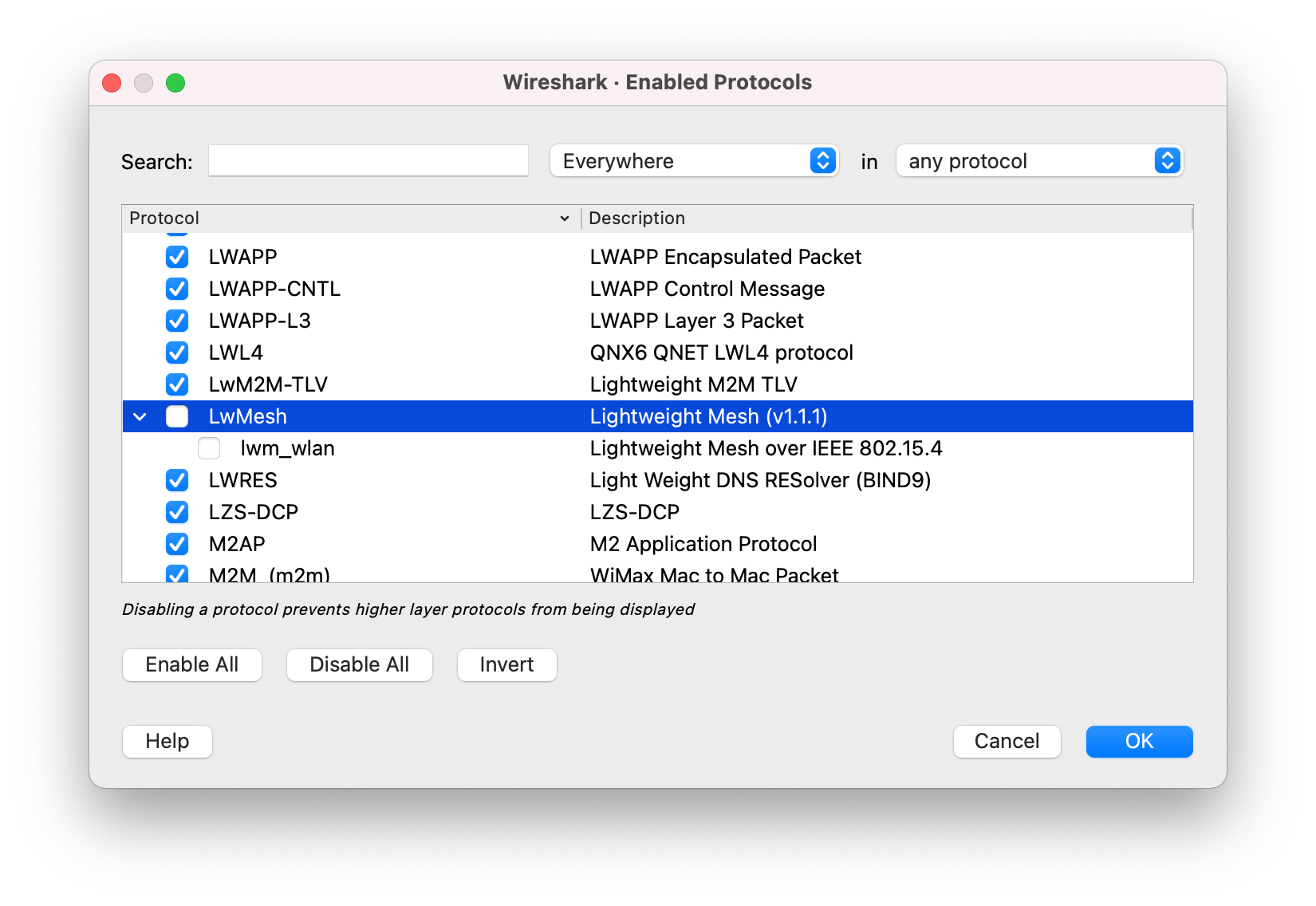
- In Wireshark, go to Analyze > Enabled Protocols....
-
In the Enabled Protocols window, disable unwanted protocols by unchecking the field next to their name.
For example, you might want to disable LwMesh, ZigBee, and ZigBee Green Power.
-
Click OK to save the settings.
Configuring Wireshark for Zigbee¶
Additional Wireshark configuration is required to start capturing data from Zigbee samples in the nRF Connect SDK or from Zigbee examples in the nRF5 SDK for Thread and Zigbee.
To capture data from Zigbee examples and samples:
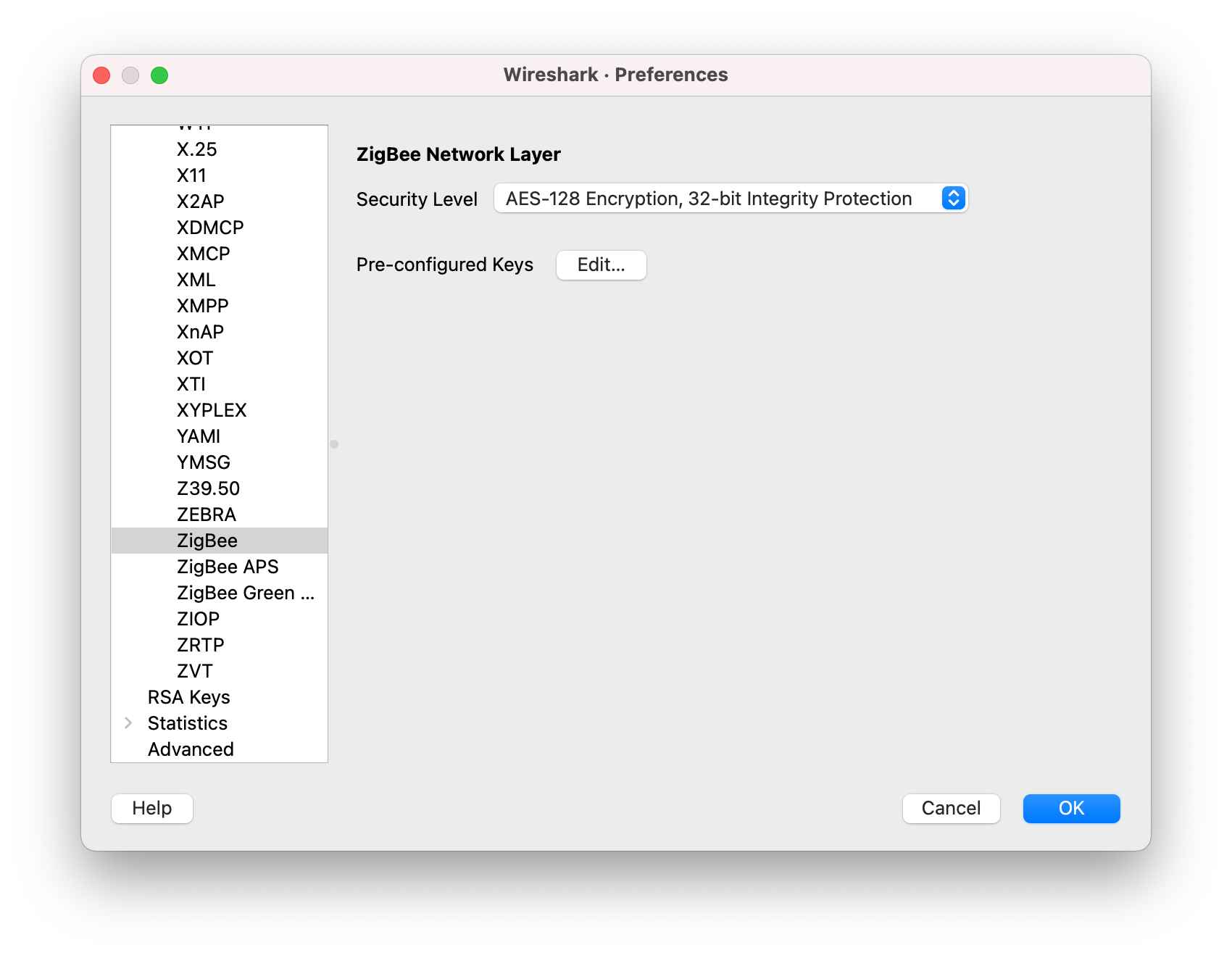
- In Wireshark, go to Edit > Preferences... (on Windows or Linux) or Wireshark > Preferences... (on macOS).
-
In the Preferences section list, go to Protocols > ZigBee.
-
Click the Edit... button to add the preconfigured keys.
-
In the Pre-configured Keys window:
- Click + and add the key
5A:69:67:42:65:65:41:6C:6C:69:61:6E:63:65:30:39with Byte Order set to Normal and Label set toZigbeeAlliance09. -
Click + and add the key
ab:cd:ef:01:23:45:67:89:00:00:00:00:00:00:00:00with Byte Order set to Normal and Label set toNordic Examples.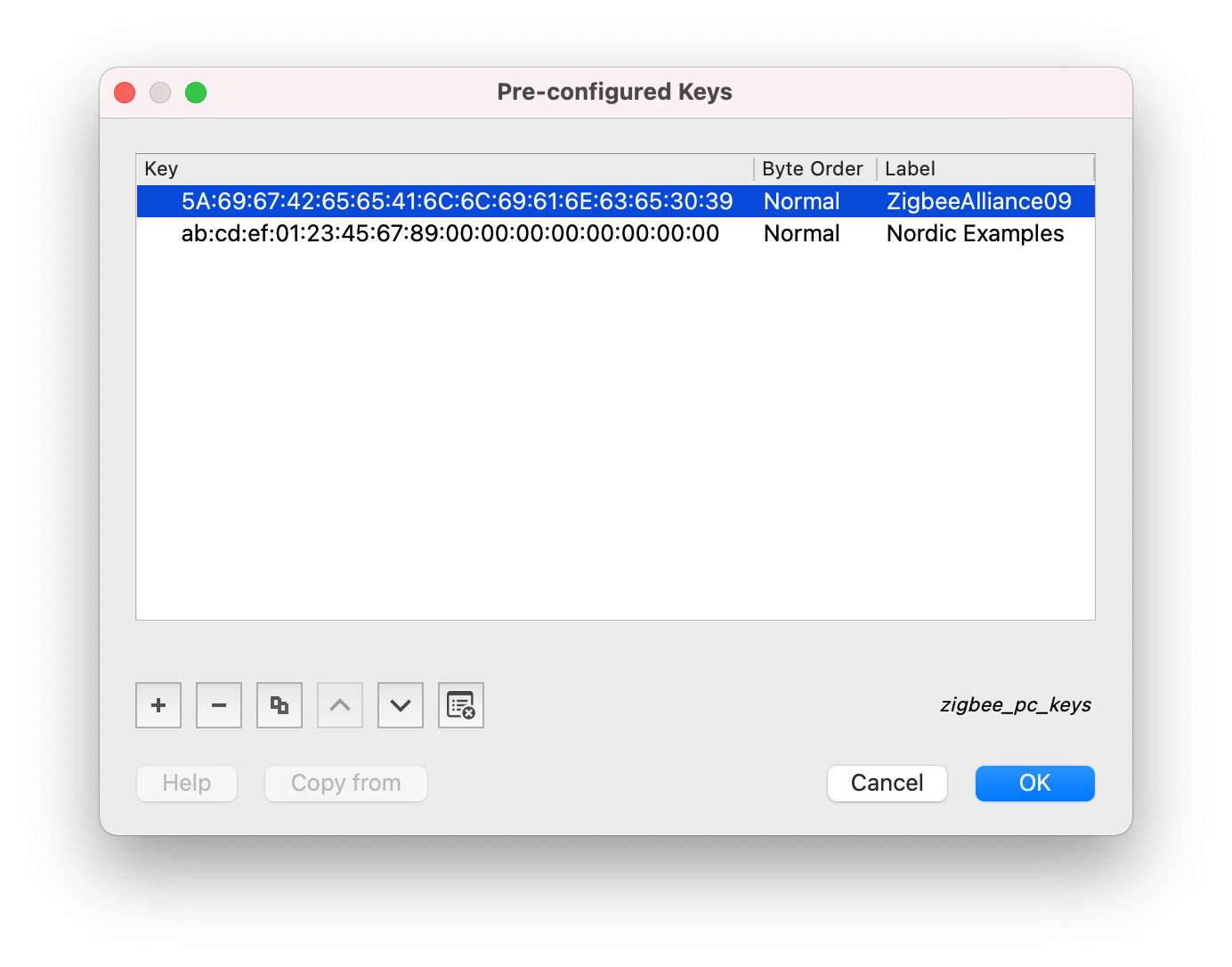
-
Click OK to close the window.
- Click + and add the key
-
Click OK to save the preferences for Zigbee.